Network Penetration Testing
- Home
- Services
Network Penetration Testing
Many businesses have already run a vulnerability assessment, so they may ask why they need to take the extra step of running Pen Tests. Penetration testing usually occurs after performing a vulnerability assessment. A vulnerability assessment has the same goals as a Pen Test, but generally, a vulnerability assessment only employs automated vulnerability scanners to spot common issues.
It’s true that vulnerability scanning can help by pinpointing security vulnerabilities. Good scans even categorize security risks, assign risk levels, and offer remediation suggestions. While it’s not the same thing as a penetration test, this kind of assessment may be used to help gather the information that will help plan the test.
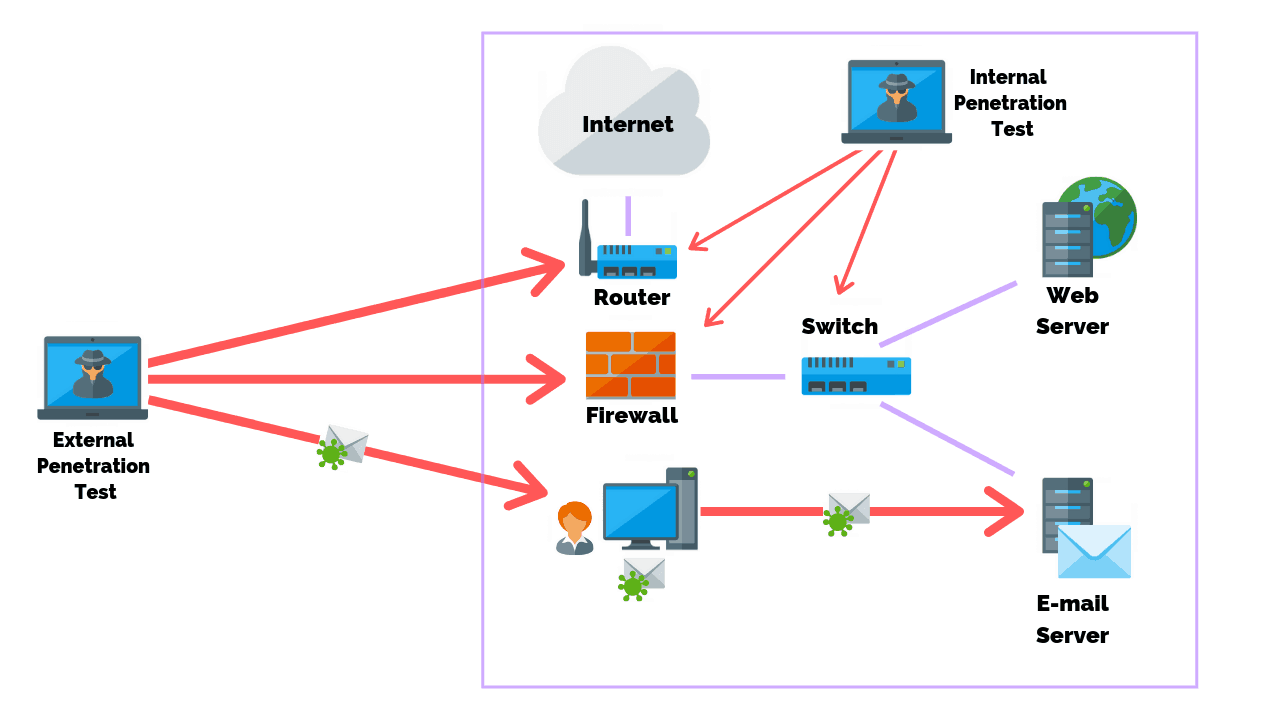
Benefits of Performing a Network Pen Test
We can offer numerous benefits to any organization concerned about security.
Some of the primary benefits of this type of Network security testing include:
- Identifying Network Security Flaws
- Understanding Risk Levels
- Mapping Out the Organization’s Overall Security Posture
- Fixing Information Security
How Long Does a Network Penetration Test Take?
The time it takes pen testers to complete their work depends on the organization’s systems’ size and complexity. Testing a one-doctor medical office won’t usually take as long as working with a global enterprise. Of course, the time the test takes may also depend upon any weaknesses or vulnerabilities uncovered and the sensitivity of the information that the security system should protect. With that said, testing projects usually last from one to four weeks. After scoping the project, the testing team can offer a detailed estimate.
Copyright @2020 Cyber Moksha | Designed Zilicon Technologies Pvt.Ltd
