Wireless Network Assessment Services & Network Security
- Home
- Services
Wireless Network Assessment Services
We identifies flaws and provides an unadulterated view of exactly how vulnerable your systems are to malicious and unauthorized accesses. Identifying misconfigurations and inconsistencies in wireless implementations and rogue access points can improve your security posture and achieve compliance with regulatory frameworks.
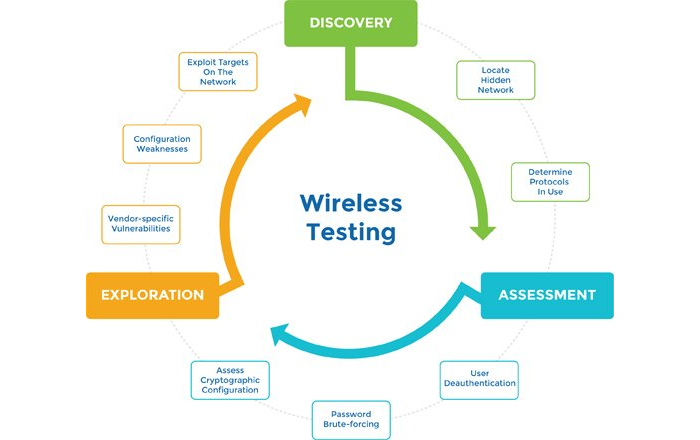
Our Wireless Network Assessment Checklist :
It helps in resolving :
- Identifying Wireless Interference
- Areas of High-Density Users
- Low-Powered Devices or Applications Accessing the Wireless Network
- Addressing the Ever-Higher Demands of Users
Copyright @2020 Cyber Moksha | Designed Zilicon Technologies Pvt.Ltd
